The traditional enterprise boundaries of a homogenous, on-premise network perimeter are vanishing before our eyes. More businesses are moving to the cloud and the lines of separation are becoming increasingly blurred. The cloud promises many benefits, but also presents some challenges that businesses must properly address—including access management challenges.
For example, most companies already struggle with managing access to their systems because users or entities require different access and permissions, including different access paths and endpoints. This complexity increases when the type of users grows from employees to contractors, third parties, service accounts and others. If your organization supports hundreds or thousands of user types already, the absence of a traditional perimeter in the cloud can make access management a daunting challenge.
As technology vendors race to provide the services and features companies require to secure ubiquitous access to their critical systems, it can be challenging to identify the right technology or set of technologies that will benefit your business. In this article, we examine traditional identity and access management (IAM) technology (also known as identity providers or IDPs), secure access service edge (SASE) tools, cloud access security brokers (CASBs) and zero-trust network access (ZTNA) tools—how they complement one another and where they differ.
Our objective is to shed light on how these different technologies can be applied to your goal of providing robust and effective adaptive access for your business.
Why does adaptive access matter in a changing business landscape?
Adaptive access has become critical as a result of the changing business landscape. Because of digital transformation initiatives, remote work and more extensive bring-your-own-device policies during the COVID-19 pandemic, organizations are adopting zero-trust models.
A zero-trust model treats every access attempt as if it originates from an untrusted network, and focuses on authenticating every user and device before granting access to any application. This model requires that devices and users be able to establish trust regardless of physical location, and no matter what kind of network they’re connecting from.
A traditional parameter-based security model is no longer the right choice, as organizations typically don’t have their data in a single place. Today, information is often spread across cloud vendors, which makes it more difficult to have a single security control for an entire network.
Access security technology can be thought of as a tool, and just as nobody would consider a hammer as the appropriate tool for sawing a piece of wood, each access tool has its place and purpose. As access becomes ubiquitous, a well-planned adaptive access strategy that includes identification of the right enabling technology for the job becomes imperative.
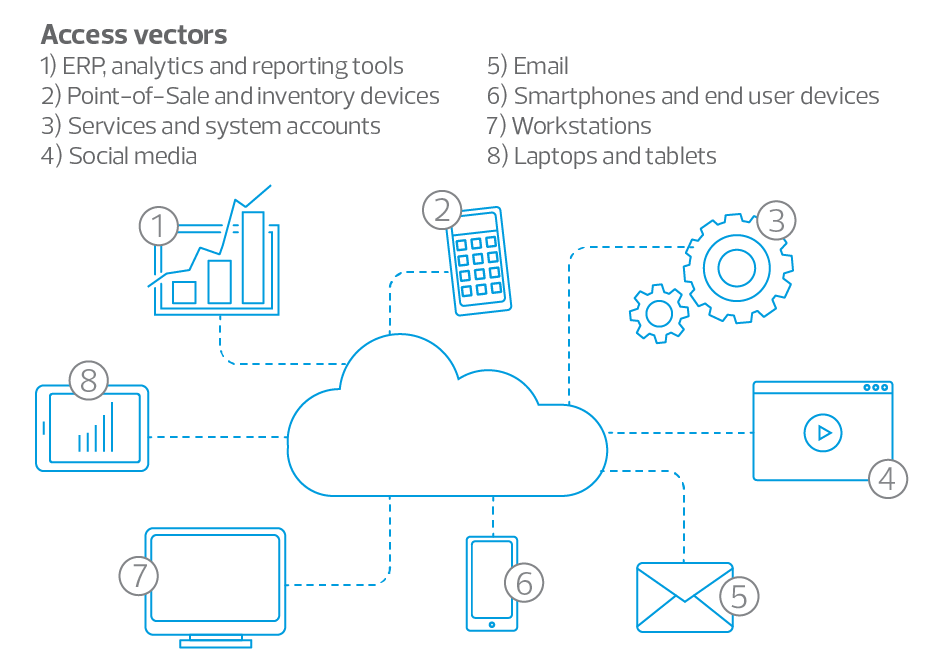
The following illustration emphasizes the various access paths and absence of a traditional perimeter at the heart of the adaptive access challenge.