The manufacturing industry continues to be a top target for cyberattacks.
Key takeaways
Manufacturers have similar risks as other sectors, but they rely more on operational technology.
As industrial policy spurs manufacturing activity, companies must proactively manage cyber risks.
As U.S. industrial policy spurs a wave of new manufacturing construction activity, companies have a unique opportunity and requirement to prioritize cybersecurity resilience during facility expansions and greenfield deployments.
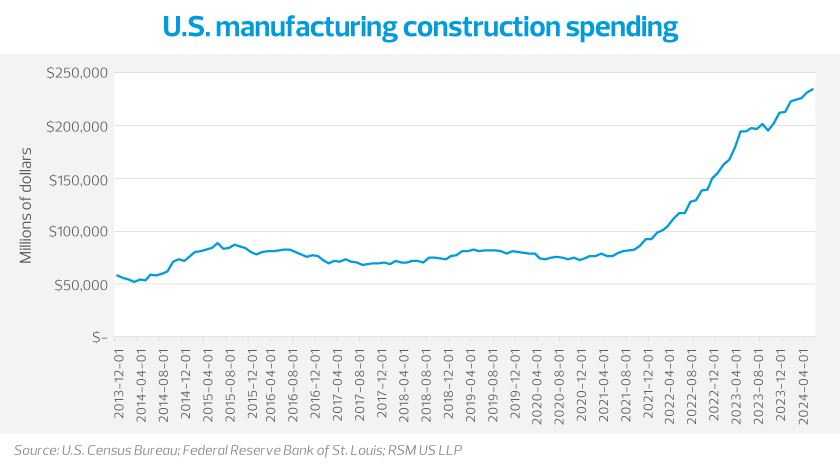
This growing need is driven by the continued deployment of Industry 4.0 ecosystems to integrate connected digital solutions throughout the manufacturing process. Manufacturers are scrambling to align their data to take advantage of new generative artificial intelligence tools and solve ongoing labor challenges. Bad actors look to take advantage of middle market businesses whose cybersecurity investments are not keeping pace with evolving technology—and the manufacturing industry continues to rank as a top target, according to IBM X-Force data.
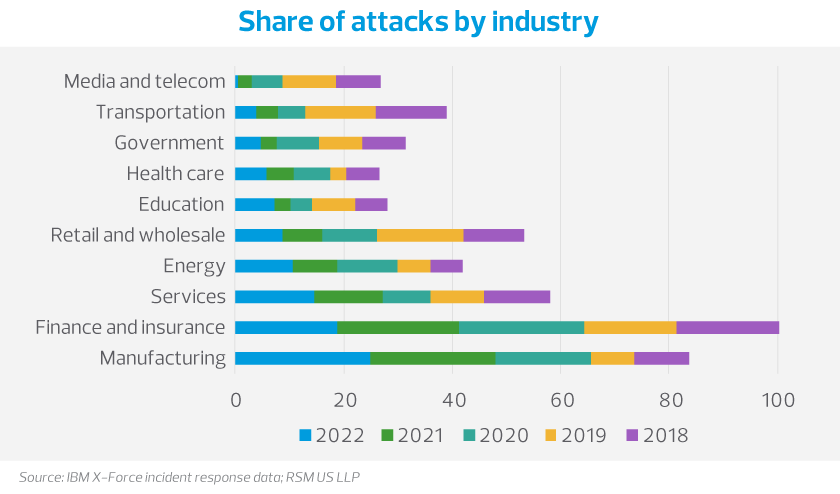
While manufacturers have many of the same risks as other industries, one thing makes them unique: their reliance on operational technology (OT). Historically, manufacturing environments were not connected to the information technology (IT) network, but they are now becoming more integrated. Additionally, manufacturers are particularly vulnerable to extortion or ransomware attacks due to their uptime requirements.
Industrial companies need to take proactive measures to manage the intensifying cyber risk environment. Here are the top five areas businesses should focus on to become more resilient:
- Internet of Things (IoT) management: As connected devices proliferate on factory floors, it can be a challenge for IT security to keep pace with the flood of new devices on the network. Strong integration between operations/engineering and IT security is required to ensure devices are not forgotten during patching and upgrade cycles.
- Segmentation: With businesses striving for more connected environments that enable AI and machine learning, the longtime silos between IT and OT environments are breaking down. But today, many environments protect only ingress and egress traffic between OT and IT networks. Looking forward, we expect deployment of more microsegmentation technologies to secure traffic at the device level within the OT environment.
- Employee training: While we can deploy unlimited cybersecurity tools to assist with prevention and detection, human error is consistently the weakest link in any environment. Many manufacturers will continue to face labor challenges for technical roles and are looking at upskilling their workforce. Security awareness is an essential component of employee training programs.
- Zero trust: With more and more systems moving to the cloud but relying on OT data, deploying technology in a zero-trust manner is crucial. Organizations need to be selective about what data is stored where and who has access to it, and require multifactor authentication and robust conditional access policies for all facets of technology.
- Cyber strategy refreshes: With the speed of change within cybersecurity, it’s imperative to always look for new ways to improve your security posture. With insurance providers asking more and more questions around protective measures, leveraging third-party assessments, audits and testing is critical.
In the manufacturing space, security professionals often struggle with legacy technology embedded in production equipment. While it might not always be financially possible to upgrade the physical production equipment, technology solutions can still help. Focusing on the areas above to manage the environment is critical as manufacturers deploy more technology on the factory floor.

